In this post a quick overview of a sample Radius server configuration for admin authentication on Comware7 devices.
Comware7 is using a complete new authorization system compared to Comware5. In Comware5, there were the 4 levels (0-1-2-3) and that was basically it.
In Comware7, there are 15 different levels and admins can define their own roles, this is known as RBAC. The big difference with command authorization is the fact that RBAC simply allows the assignment of interfaces, features and Read/Write options, so you can easily grant full access to interface x , while preventing admin access to interface y.
Once you have defined new roles, you just need to assign them at login time to the correct user through the TACACS+ or RADIUS server.
In this article, the RADIUS server is configured and the default role “network-admin” is assigned to the network administrator.
Configuration steps:
- Define a Windows group and test user
- RADIUS Server: RADIUS Client Configuration (not part of this article)
- RADIUS Server: Network Policy configuration to grant network-admin role
- Comware7 Device: RADIUS Server configuration
- Comware7 Device: Domain and line configuration
- Verify
- Network trace
The article has been tested with an HP 5900 R2307, Simware7 7.1.45 and the VSR1000 E0102.
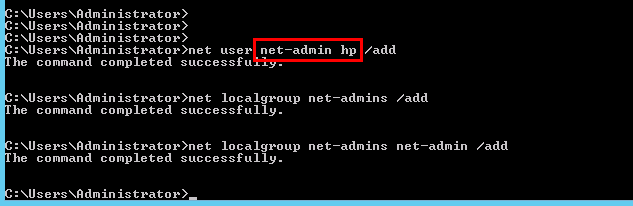
Define a Windows group and test user
In this step a sample Windows group is created, a test user “net-admin” is defined and the user is made a member of the group.
RADIUS Server: Network Policy configuration
In this example, the Microsoft NPS Server is used. Install the NPS Server role on a Windows system and define a RADIUS client for the switch (steps not included in article).
Open the Network Policy Server management console.
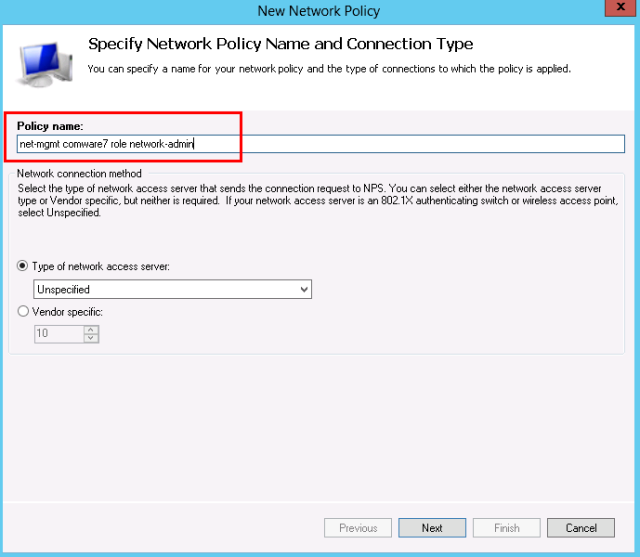
- Next, define a new Access Policy:
- Enter a descriptive name for the policy.
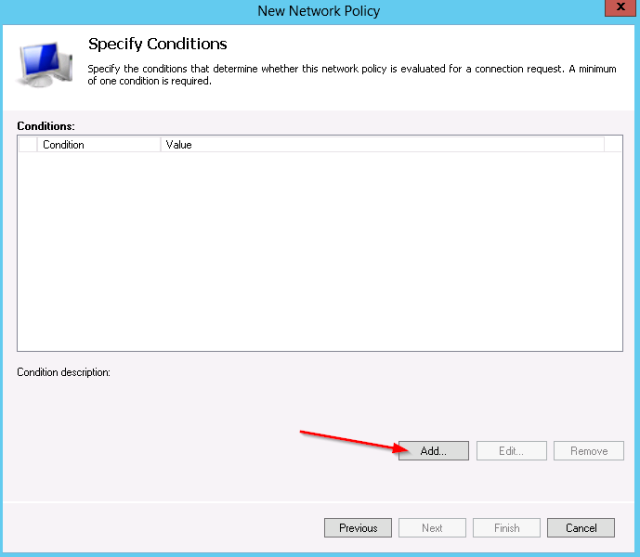
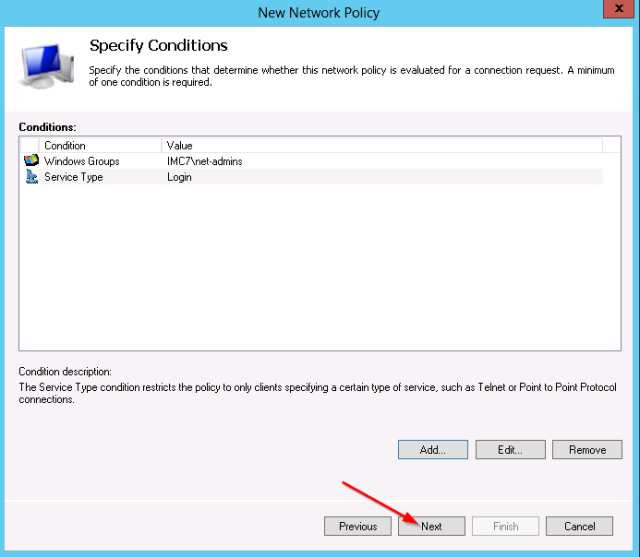
- Next you need to set the matching conditions for this policy. This example will check on:
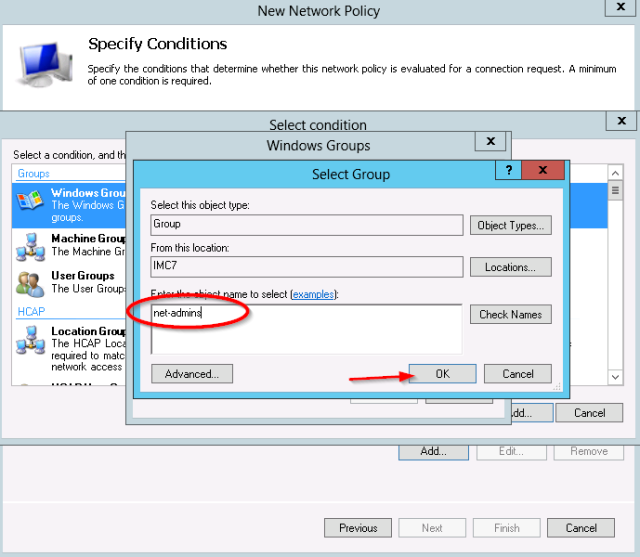
- Windows group “net-admins”
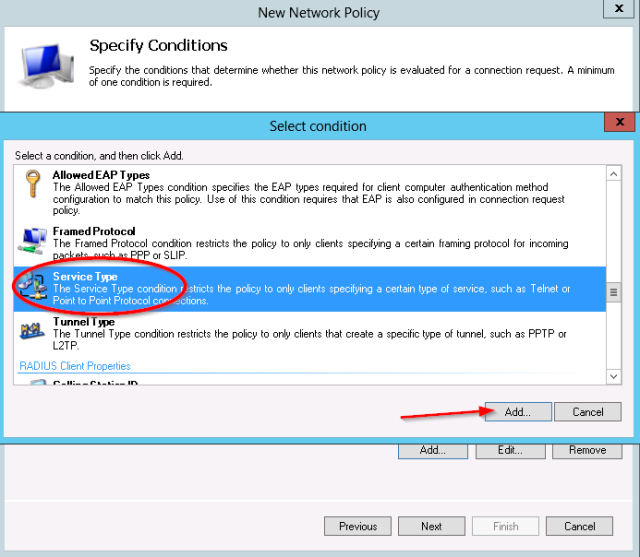
- Service-type “login”
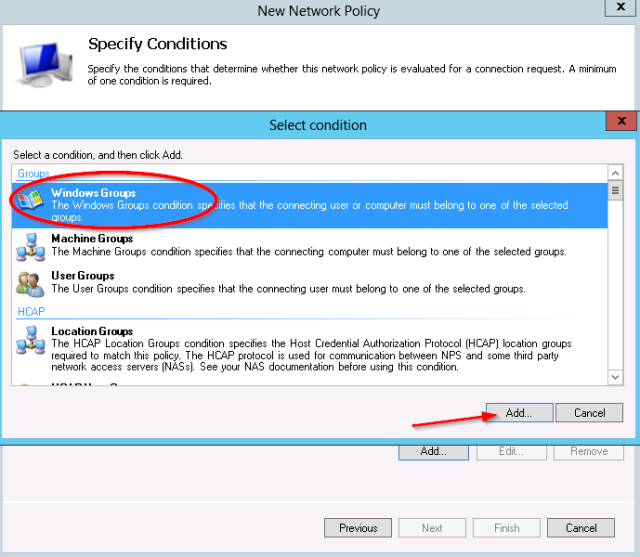
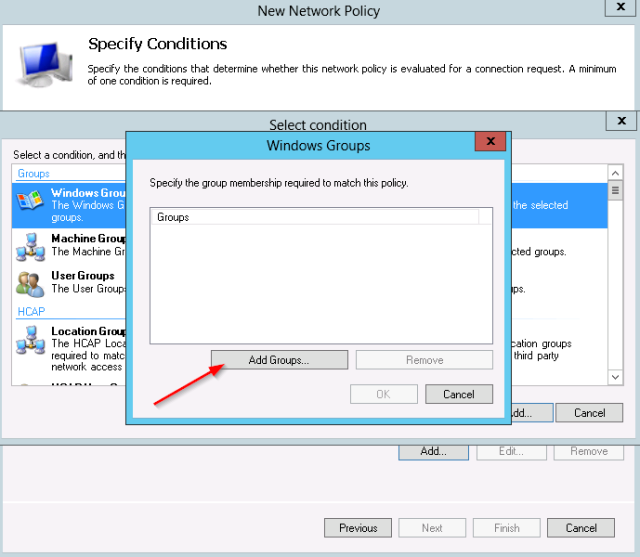
- First add the Windows group condition:
- The test group “net-admins” is selected.
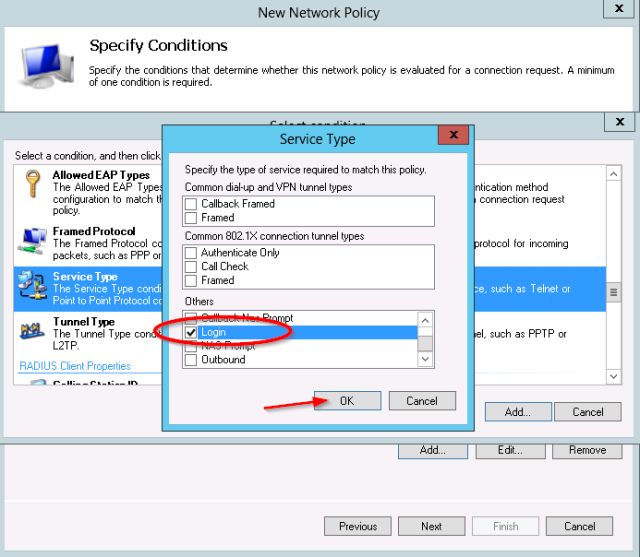
- Next add the service-type condition:
- For the Service-Type, select “Login”
- Verify the 2 conditions:
- Leave the access permission to “access granted“
- Admin logins are basic RADIUS login requests, so make sure to enable the clear text PAP/SPAP methods:
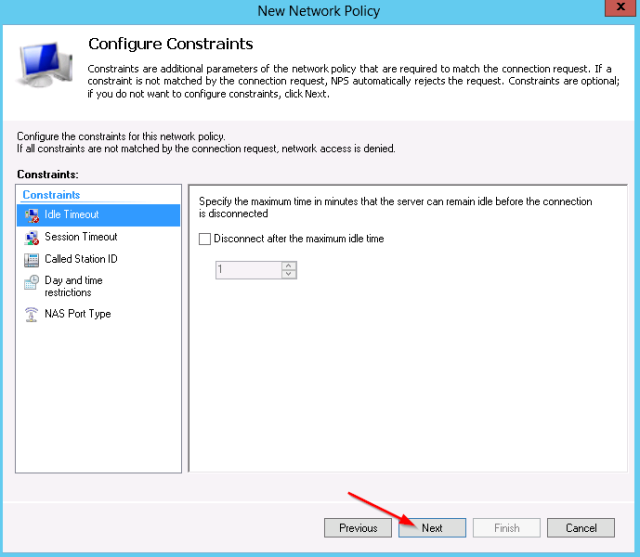
- No other constraints need to be configured:
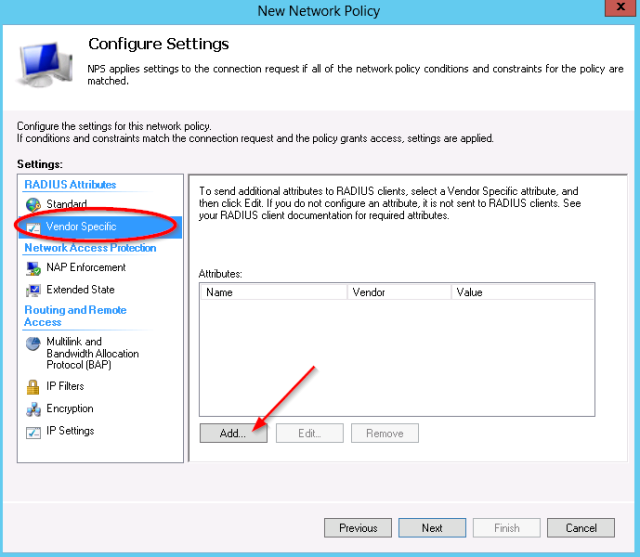
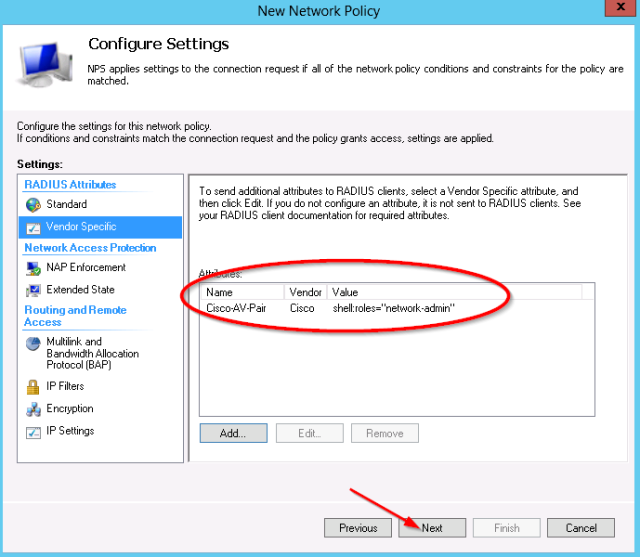
- In the settings which will be applied, select the “Vendor Specific” category.
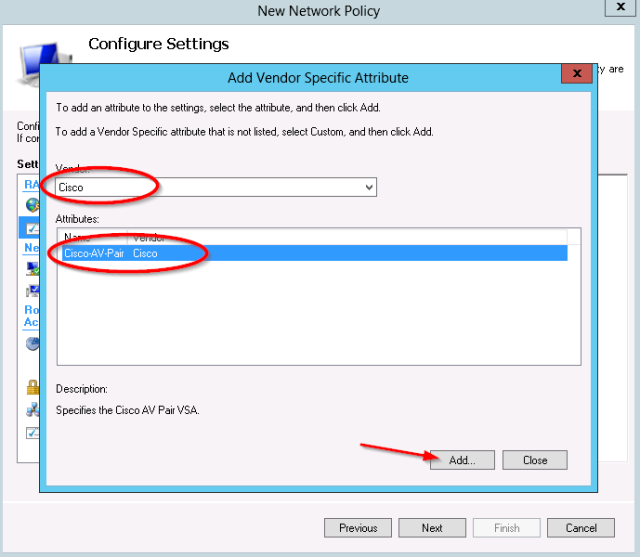
- Select the vendor “Cisco” and the “Cisco-AV-Pair” Attribute:
- UPDATE 19/01/2015: I received input through the comments that currently the quotes are no longer required, so the command would now be shell:roles=network-admin (no more quotes). I have not checked this myself, but consider yourself updated now :). The screenshots in this post have not been updated to reflect this update !
- Original post text:
For the attribute value, set shell:roles=”network-admin”
- Review the Vendor Specific settings and finish the wizard.
- In the Network policy list, make sure the new policy is placed in front of the block all default policies:
Comware7 Device: RADIUS Server configuration
On the comware7 device, define a radius scheme. The simple password will be automatically saved with a ciphered version. Make sure the key matches the RADIUS Client definitions on the NPS server.
radius scheme nps primary authentication 10.0.1.100 primary accounting 10.0.1.100 key authentication simple hp key accounting simple hp user-name-format without-domain #
Comware7 Device: Domain and line configuration
Next, configure an isp domain (in this example, the default domain system is updated) to use the radius server for administrative logins. Backup authentication is set to none in this example.
domain system authentication login radius-scheme nps none authorization login radius-scheme nps none accounting login radius-scheme nps none #
Configure the line vty range to use the domain authentication scheme
line vty 0 63 authentication-mode scheme
Verify the authentication
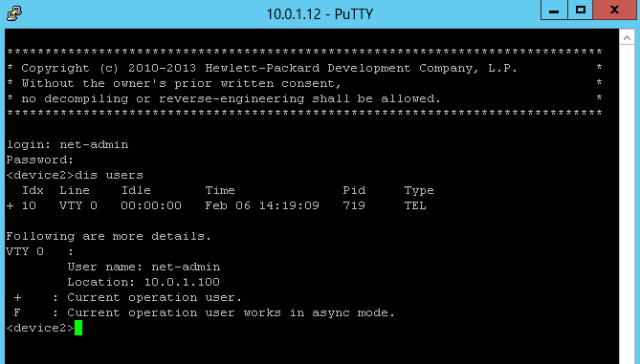
Now a telnet client connection is opened, and the test user “net-admin” can login to the device:
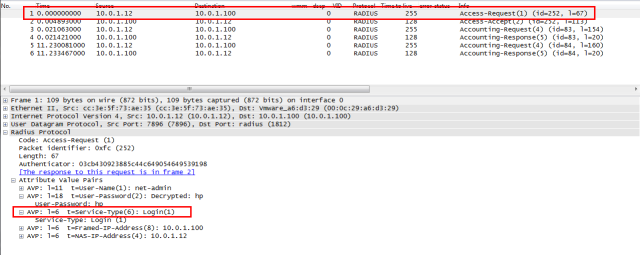
RADIUS network trace
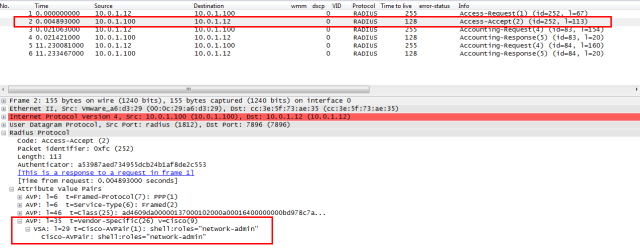
- And the access accept shows the assigned network role
Comware roles
Admin roles can be listed on the comware device with the “display role” command.
This is the filtered example:
<device2>dis role | i Role Role: network-admin Role: network-operator Role: level-0 Role: level-1 Role: level-2 Role: level-3 Role: level-4 Role: level-5 Role: level-6 Role: level-7 Role: level-8 Role: level-9 Role: level-10 Role: level-11 Role: level-12 Role: level-13 Role: level-14 Role: level-15 Role: security-audit
And this would be the detail of the role network-admin:
<device2>dis role name network-admin Role: network-admin Description: Predefined network admin role has access to all commands on the device VLAN policy: permit (default) Interface policy: permit (default) VPN instance policy: permit (default) ------------------------------------------------------------------- Rule Perm Type Scope Entity ------------------------------------------------------------------- sys-1 permit command * sys-2 permit RWX web-menu - sys-3 permit RWX xml-element - sys-4 deny command display security-logfile summary sys-5 deny command system-view ; info-center securi ty-logfile directory * sys-6 deny command security-logfile save R:Read W:Write X:Execute <device2>









Very informative article, thank you. However, I get access denied. 😦
I would recommend to run through the configuration again and check each step:
* radius server : client IP and secret
* radius server : check logs (accept/reject)
* radius server : verify the vendor-specific Cisco-AVPair does not contain any typo’s
* comware device : make sure authentication/accounting and authorization are configured under the domain (I had a recent case where only authentication and authorization were configured, which also caused an access denied)
* comware device : configure radius authentication and accounting and the key (secret) for both
* comware device : perform radius debugging and verify access-accept packets are received from the radius server
Thank you very much Peter.
After hours with RADIUS authentication issue i look your article and this answer, nice.
Everything works fine now.
saved my friday hahaha
The logfile stated that I was denied because there was no corresponding Connection Request Policy. Created that and it works. It seems that when I get AAA to work, local password authentication is no longer possible. Do you know a way to combine RADIUS and local passwords?
I enabled uthentication-mode scheme only on first 16 vty lines as seen in the display command:
switch]dis line vty 5
Idx Type Tx/Rx Modem Auth Int
15 VTY 5 – A –
30 VTY 20 – P –
So, in theory, should I not be able to authenticate with the local password if I connected on vty 20?However, I have no idea if it is possible to specify a vty line at login.
Hi Johan,
this is fairly simple through the domain concept. The post example configured the domain system with radius authentication, the domain system is also the default domain.
This means that any login without the @ sign will be processed by the default domain (system). So a login “admin” will be processed like this, but a login “admin@system” would also be processed like this.
So if you want to have local and remote, you must use 2 domains:
1/ Keep e.g. domain system as default (default domain and default local user auth), define e.g. a local user “admin”
2/ Define a new domain e.g. “central”, and configure the login radius auth on this domain. I assume a central radius user “net-admin” exists with proper configuration.
Now at the vty login, you can login with:
1/ admin > there is no @ sign, so default domain is used (system), which is still using the local auth
2/ net-admin@central > @ sign, so the switch will process the “net-admin” username based on the “central” domain settings. These point to radius > radius login will be done. The radius server setting has “username-format without domain”, so the login request to the radius server will be username “net-admin”. Otherwise (username-format with domain), the login request to the radius server would be “net-admin@central”.
So within a domain, only 1 method is possible (you can use local as backup if radius failed, but not “concurrent” login and radius).
I hope this clarifies the setup !
And I forgot you can also reverse the default domain to the central (radius),so at the vty login:
1/ admin@system > will use the domain system with local auth
2/ net-admin > no @ sign, so use the default domain (configured to central) with radius
Hi Peter,
Very helpful page, thanks for the info. You say that within a domain you can use local authentication as backup if radius fails – could you just clarify how that is done please? Is that what “authentication login radius-scheme xxx local” means, because “local” is listed after the radius scheme?
Thanks!
Hi Dominic,
Yes, the local keyword means the local user database will be used as backup in case the primary authentication method would be down
Also – apologies for the double post! – how does the Comware device decide when radius is unavailable in that scenario? Is it a ping to the specified IP address(es)?
Thanks again.
That is controlled by several configuration options:
1/ check of single radius server
Each radius scheme can be configured with a primary and secondary radius server IP, so effectively 2 radius servers can be configured.
The device will by default send the radius request to the primary server, at which point a timer is started (timer response-timeout).
When the device does not receive a response (for whatever reason) within this timer period, it will resend the request (retry) and wait again.
It will repeat this based on the configured “retry” value.
Once all retries have failed, the single (by default primary) server status will be set to a BLOCKED state, which means it will not be used by the device anymore.
If a secondary server has been configured on the radius scheme, the secondary (backup radius server) will be used at this point.
The original radius server will remain in the BLOCKED state (not used) for the period configured by the quiet configuration parameter.
Once the timer expired, the status changes to ACTIVE again and the device will attempt to use it again (based on first rules), if it fails again, it changes to BLOCKED again.
radius scheme uam
# wait timer for respone (default 3s)
timer response-timeout 3
# number of attempts (default 3) > default total 9 seconds
retry 3
# how long a failed server is in blocked state (default 5 min)
timer quiet 5
Above system will ensure:
* detection of failed radius
* avoids loosing time on every request to reach the original radius (thanks to the 5 min blocked state)
* auto-recovery of using the primary radius if it comes back online (after 5 min timer expires)
2/ failover of the primary authentication method to the secondary authentication method
While rules above provide failover for primary/secondary radius, it could happen that the network is down or both radius servers are down.
In this case, both primary and secondary servers will be in BLOCKED state, and the radius scheme object will be marked as failed.
At this point, the secondary authentication method which can be configured on the domain scheme will be used (for example the local user database).
Worked just like you said. Thanks a lot for your help!
Glad to hear it worked !
Very Informative article as always.. and even useful info in comment section!
I am trying to configure domain system by a user logged in via telnet and i am getting the following error message:
[HP]authorization default hwtacacs-scheme tacacs+ local
There are user(s) online ,can not be configured.
Under line vty 0 63 i do have authentication-mode scheme, which is using AAA for authentication but if i dont have console access, is their a way i can login via vty locally rather than scheme?
The easiest method will be to have a multi-step approach:
1/ reconfigure lint vty 0 1
configure password and set it to auth mode password
2/ connect again with telnet, this should be with the password auth (this will ensure not scheme logins are active)
3/ reconfigure the domain system
4/ use additional telnet connections (the 3th telnet connection will be vty 3, which is still set to use the scheme auth) to test the new system
5/ if validated ok, change the vty 0 1 to auth scheme again
Thanks a lot for the valuable input, i was able to resolve the issue, but just to add a point, for one of ours routers in the DVPN network having the role as VAM server, we were not able to execute the command authorization default hw-tacas ABC local under domain system,
I tried it on another VAM Server router which was disconnected from uplinks and it took the command, so i concluded the user created with service-type dvpn with Spokes/Hubs registered might also interfere with the process of configuring tacacs server.
true, if you follow the default setup/config of the dvpn, a local user is defined e.g. dvpn-user, and on the remote end side, the username you enter would be “dvpn-user”. Since no @ sign is used, it will be authenticated using the default domain (which is system by default).
So you would either have to change the default domain, or create a new domain for the dvpn users , e.g. dvpn-domain (default settings should be ok, since it uses local users for the auth), and configure the remote end to login with dvpn-user@dvpn-domain. That would ensure the logins are not processed by the default system domain.
Thanks for your replies to both my questions – very helpful!
Hello
First thank you for this clear howto.
I’m having an issue on 5900 devices. I followed your howto, I can connect using SSH but then I get immediately disconnected.
lscharf@10.xx.xx.xx‘s password:
******************************************************************************
* Copyright (c) 2010-2014 Hewlett-Packard Development Company, L.P. *
* Without the owner’s prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
Connection to 10.xx.xx.xx closed.
I have 2 VTY lines and I can’t delete the second one, I don’t know if that could impact anything.
line vty 0 15
authentication-mode scheme
user-role network-operator
protocol inbound ssh
idle-timeout 30 5
#
line vty 16 63
authentication-mode scheme
user-role network-operator
Do you have any idea where this could be coming from ?
Many thanks beforehand.
Léo
Hi Leo,
This is because there is a range of 64 (0 to 63) telnet sessions which can be configured (so you could have 64 concurrent telnet connections, the first connecting user would be on vty 0, the second telnet session on vty 1 etc).
In your case, the first 16 sessions have a different configuration from the remaining telnet sessions. When you would ensure that they have the same config, the switch will show them on 1 line again.
E.g.:
line vty 16 63
protocol inbound ssh
idle-timeout 30 5
That will ensure all telnet sessions have the same settings, so the config can show them as 1 range (line vty 0 63) again.
As far as the ssh disconnect is concerned, you would need check the log files on the radius server and/or the log messages on the device (display log reverse).
Best regards,Peter
Hey, just wanted to add that shell:roles=”network-admin” should be without hyphens. Like this shell:roles=network-admin. Otherwise the switch won´t eat it 😀
Yep, that was actually my issue in my previous comments.
That should be corrected in your tutorial 😉
Thanks.
Hi Leo, Dennis, I have included an update text in the post to warn readers, thank you for the comments !
Hi Dennis,
Which switch/firmware release did you use for this ?
I remember having to try various formats and at the time, this version with quotes did work for me (many other formats did not 🙂 ).
So I am curious if this has changed at some point…
thanks !
I’m using “HP Comware Software, Version 7.1.045, Release 2311P01”
Hi,
I am trying to setup the backup authentication as local, for when Radius is not available, but, I cannot get it to work:
here is my configuration and I am testing by disabling the Radius policy for this device:
user-interface vty 0 15
authentication-mode scheme
user-role network-admin
user-role network-operator
protocol inbound ssh
radius scheme switch-radius
primary authentication x.x.x.x
primary accounting x.x.x.x
secondary authentication x.x.x.x
secondary accounting x.x.x.x
key authentication cipher key
key accounting cipher key
user-name-format without-domain
#
radius scheme system
user-name-format without-domain
#
domain OURDOMAIN
authentication login radius-scheme switch-radius
authorization login radius-scheme switch-radius
accounting login radius-scheme switch-radius
#
domain system
authentication login radius-scheme system local
authorization login radius-scheme system local
accounting login radius-scheme system local
local-user adminclass manage
password hash password
service-type ssh telnet
authorization-attribute user-role network-operator
authorization-attribute user-role network-admin
domain default enable OURDOMAIN
role default-role enable
Thanks for help
Hi, you should update the domain configuration and add the local auth option as fallback:
domain OURDOMAIN
authentication login radius-scheme switch-radius local
authorization login radius-scheme switch-radius local
accounting login radius-scheme switch-radius local
We were running 7.1.035 release 2210 on our 5920s, with RADIUS-authenticated SSH access as described above. Since upgrading to version 7.1.045 release 2311P05, this access no longer works – the SSH user is rejected with a “login failed” message, and the following log messages appear on the console port:
SSHS/6/SSHS_LOG: Accepted password for user123 from 1.2.3.4 port 1346 ssh2.
SSHS/6/SSHS_CONNECT: SSH user user123 (IP: 1.2.3.4) connected to the server successfully.
LOGIN/6/LOGIN_FAILED: user123 failed to log in from 1.2.3.4.
SSHS/6/SSHS_LOG: User user123 logged out from 1.2.3.4 port 1346.
SSHS/6/SSHS_DISCONNECT: SSH user user123 (IP: 1.2.3.4) disconnected from the server.
I saw the blog update about the use of quotes in the Cisco-AV-Pair attribute, so changed our config from shell:roles=”network-admin” to shell:roles=network-admin (no more quotes). Unfortunately this hasn’t solved the problem. I was just wondering if we are aware of anything else which has changed?
Apologies, should have looked more closely before posting last comment.. it was just our domain command “accounting primary x.x.x.x” which was missing!
Hey Peter, just wanted you to know this article is still helping people out there, coming from a Cisco shop this was extremely helpful. After hours of troubleshooting I remembered that my radius client key was set to a test value for the Comware 7 switch I was testing. Great article, much easier to read that HP’s stuff
Thank you Chris, that is very nice to hear!
Hi, I got a problem with my setup…
I followed the tutorial and I’m able to connect to the switch. Unfortunately, the user role don’t seems to be applied. I get an “Permission denied.” on every command…
I already tried to set the Cisco AV Pair value with and without quotes, with no change at all.
I never get to the prompt after this setup while trying SSH login to the switch
Server 2012 R2 NPS
NOT even with local user!!
login as: me
me@10.0.1.190‘s password:
******************************************************************************
* Copyright (c) 2010-2015 Hewlett Packard Enterprise Development LP *
* Without the owner’s prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
Great article. Did the job for me. Thanks
Hi, Im trying this with a HPE 5120 SI with version 5.20, Release 1518
I cannot get it to login with highest privileges. I’ve tried the vendor spesific method and user-interface vty 0 15 -> user privilede level 3 but nothing seems to do the job.
It just says:
>sys
^
% Unrecognized command found at ‘^’ position.
Can you provide more detail about the specific options you configured?
See this link for an example of the older cmw5 systems:
http://hpnetworkers.blogspot.nl/2011/05/hp-series-h3c-comware-radius.html
Hi, I’m trying to configure a HP A5120-24G-PoE+ EI. I was able to login but can’t switch to system-view. I’m stuck at user-view. Here is the config:
domain default enable seldp
#
radius scheme system
user-name-format without-domain
radius scheme switch-radius
primary authentication 10.0.3.254 10812
primary accounting 10.0.3.254
key authentication ANYKEY
key accounting ANYKEY
user-name-format without-domain
#
domain seldp
authentication login radius-scheme switch-radius local
authorization login radius-scheme switch-radius local
accounting login radius-scheme switch-radius local
authentication super radius-scheme switch-radius
access-limit disable
state active
idle-cut disable
self-service-url disable
domain system
access-limit disable
state active
idle-cut disable
self-service-url disable
#
user-group system
#
local-user admin
password cipher ***********
authorization-attribute level 3
service-type telnet terminal
local-user sshadmin
password cipher ************
authorization-attribute level 3
service-type ssh
#
user-interface vty 0 4
authentication-mode scheme
user-interface vty 5 15
#
hello, good post, some-one can tell me what will be the configuration for the GE port in the Switch?